- Record: found
- Abstract: found
- Article: found
A Role-Based Access Control Model in Modbus SCADA Systems. A Centralized Model Approach
Read this article at
Abstract
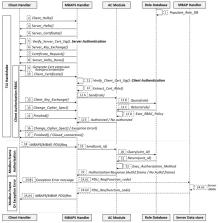
Industrial Control Systems (ICS) and Supervisory Control systems and Data Acquisition (SCADA) networks implement industrial communication protocols to enable their operations. Modbus is an application protocol that allows communication between millions of automation devices. Unfortunately, Modbus lacks basic security mechanisms, and this leads to multiple vulnerabilities, due to both design and implementation. This issue enables certain types of attacks, for example, man in the middle attacks, eavesdropping attacks, and replay attack. The exploitation of such flaws may greatly influence companies and the general population, especially for attacks targeting critical infrastructural assets, such as power plants, water distribution and railway transportation systems. In order to provide security mechanisms to the protocol, the Modbus organization released security specifications, which provide robust protection through the blending of Transport Layer Security (TLS) with the traditional Modbus protocol. TLS will encapsulate Modbus packets to provide both authentication and message-integrity protection. The security features leverage X.509v3 digital certificates for authentication of the server and client. From the security specifications, this study addresses the security problems of the Modbus protocol, proposing a new secure version of a role-based access control model (RBAC), in order to authorize both the client on the server, as well as the Modbus frame. This model is divided into an authorization process via roles, which is inserted as an arbitrary extension in the certificate X.509v3 and the message authorization via unit id, a unique identifier used to authorize the Modbus frame. Our proposal is evaluated through two approaches: A security analysis and a performance analysis. The security analysis involves verifying the protocol’s resistance to different types of attacks, as well as that certain pillars of cybersecurity, such as integrity and confidentiality, are not compromised. Finally, our performance analysis involves deploying our design over a testnet built on GNS3. This testnet has been designed based on an industrial security standard, such as IEC-62443, which divides the industrial network into levels. Then both the client and the server are deployed over this network in order to verify the feasibility of the proposal. For this purpose, different latencies measurements in industrial environments are used as a benchmark, which are matched against the latencies in our proposal for different cipher suites.
Related collections
Most cited references35
- Record: found
- Abstract: not found
- Article: not found
An experimental investigation of malware attacks on SCADA systems
- Record: found
- Abstract: not found
- Article: not found
Attack taxonomies for the Modbus protocols
- Record: found
- Abstract: not found
- Article: not found